Букмекерская контора Pin UP ru
Каждый молодой оператор старается ярко зайти на беттинговый рынок с целью быстрого привлечения к себе внимания большого числа потенциальных клиентов. По такому пути пошел и БК Pinup ru. Букмекер с 2016 года работает на международной арене, отличаясь неплохими условиями. Что может предложить своим пользователям лицензионный проект, впервые давший возможность сыграть осенью 2020 года?
Преимущества
Многочисленные бонусы и акции с простыми правилами отыгрыша фрибетов Высокие коэффициенты Привлекательные условия игры в разделе «Киберспорт»
Недостатки
Отсутствует мобильное приложение для iOS Низкие лимиты вывода выигрыша
Год основания: 2020
Лицензия: ФНС России (№28 от 10.10.2014)
Владелец: ООО «Уильям Хилл»
Языки техподдержки: Русский
Live чат: Да
Номер телефона: Да
Языки сайта: Русский
Версии сайта: Android, iOS, Web
Мобильная версия: Да
Разрешено в России: Да
Остров Мэн, Бахрейн, Багамы, Бангладеш, Вьетнам, Узбекистан, Уругвай, Туркменистан, Сирийская Арабская Республика, Синт-Мартен, Саудовская Аравия, Сент-Китс и Невис, Эфиопия, Индонезия, Иордания, Монако, Беларусь, Лихтенштейн, ОАЭ, Руанда, Катар, Оман, Норвегия, Остров Норфолк, Мавритания, Кувейт, Пуэрто-Рико, Палау, Пакистан, Гибралтар, Эстония, Египет, Джибути, Чешская Республика, Хорватия, Камбоджа, Буркина-Фасо, Остров Буве, Ботсвана, Бермудские острова, Гуам, Ирландия, Ямайка, Северные Марианские острова, Нидерландские Антильские острова, Марокко, Черногория, Маврикий, Маршалловы острова, Латвия, Кыргызстан, Косово, Казахстан, Джерси, Барбадос, Все, где запрещен беттинг и гемблинг, Саба, Бонайре, Аруба, Люксембург, Того, Тимор-Лешти, Таджикистан, Шри-Ланка, Самоа, Нигер, Непал, Статиа, Армения, Новая Каледония, —, Финляндия, Страны, в которых ставки на спорт запрещены на законодательном уровне, Виргинские острова (США), Внешние малые острова (США), Голландские Вест-Индские острова, Голландская Вест-Индия, Синт-Эстатиус и Саба, Голландия, Киргизия, Молдова, Монголия, Молдавия, Мальдивы, Кот-д’Ивуар, Ватикан, Реюньон, Майотта, Мартиника, Канаваке, Япония, Гваделупа, Южные Французские Территории, Каймановы острова, Антигуа и Барбуда, Сен-Пьер и Микелон, Бразилия, Бурунди, Малави, Мадагаскар, Лесото, Гамбия, Габон, Фарерские острова, Экваториальная Гвинея, ДР Конго, Коморские Острова, Чад, ЦАР, Южная Африка, Азербайджан, Палестина, Иран, Венгрия, Гонконг, Гондурас, Гаити, Гайана, Гватемала, Гренландия, Греция, Германия, Гана, Ирак, Израиль, Кения, КНДР (Корейская Народно-Демократическая Республика), Северная Македония, Нигерия, Никарагуа, Мьянма, Мозамбик, Мексика, Малайзия, Макао, Литва, ЛНДР (Лаосская Народно-Демократическая Республика), Сальвадор, Эквадор, Доминиканская Республика, Бельгия, Белоруссия, Австралия, Аргентина, Ангола, Афганистан, Франция, Испания, Великобритания, Италия, Канада, Белиз, Боливия, Босния и Герцеговина, Дания, Чехия, Куба, Коста-Рика, Конго, Колумбия, Китай, Чили, Камерун, Болгария, Британские Виргинские острова, США, Австрия, Мали, Ливия, Либерия, Ливан, Гвинея-Бисау, Гвинея, Французская Полинезия, Французская Гвиана, Эритрея, Центрально-Африканская Республика, Йемен, Мальта, Северная Корея, Сьерра-Леоне, Американское Самоа, Алжир, Албания, Кюрасао, Сен-Мартен, Арубу, Кипр, Нидерланды, Зимбабве, Судан, Сомали, Венесуэла, Вануату, Замбия, Словения, Словакия, Сингапур, Сербия, Румыния, Португалия, Польша, Филиппины, Перу, Парагвай, Папуа–Новая Гвинея, Южно-Африканская Республика, Южный Судан, Сирия, Украина, Уганда, Турция, Тунис, Тринидад и Тобаго, Таиланд, Танзания, Тайвань, Швейцария, Швеция, Суринам, Панама
Другие продукты: Быстрые ставки, Киберспорт
Live ставки: Да
На прочие события: Нет
Мультиставки: Нет
Заявки на вывод: до 3 дней
Статистика событий: Да
Приветственный бонус: 30 000 RUB Получить бонус
О БК Pin Up ru
Компания принадлежит ООО «Уильям Хилл». Это вводит многих бетторов в заблуждение. Они считают, что букмекерская контора Pin UP ru представляет на российском рынке широко известного британского оператора. Но William Hill никакого отношения к рассматриваемой БК не имеет.
Pinup ru работает через Второй ЦУПИС. Букмекер выделяется привлекательной бонусной программой — проводит викторины и турниры с неплохим призовым фондом.
Историческая справка
В 2014-м руководство конторы поставило перед собой задачу — по франшизе William Hill выйти на российский рынок. Переговоры с представителями британского оператора сильно затянулись. И в 2016-м стал действовать международный проект, работающий по лицензии Кюрасао. По словам операционного директора компании, Владимира Горева, легальная контора должна была начать деятельность намного раньше 1 октября 2020-го. Но наступившая пандемия помешала это сделать.
Лицензия
Документ выдан ФНС России под №28 от 10.10.2014-го. Получен ООО «Уильям Хилл», зарегистрированным в г. Москве.
Минимальная и максимальная ставка
Максимальный выигрыш по ставке составляет 5 млн рублей.
Минимальный лимит пари — 10 RUB. Максимальный зависит от спортивного направления и рейтинга матча.
Коэффициенты и маржа
БК Pinup ru по уровню коэффициентов превосходит многих беттинговых операторов. В этом можно убедиться на конкретном примере.
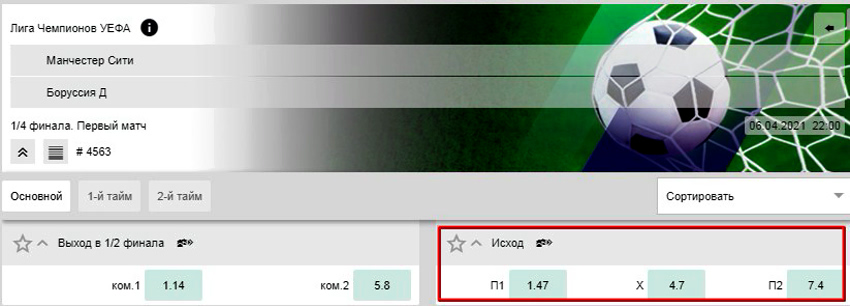
Линия на матч «Манчестер Сити» — «Боруссия Дортмунд»
На победу хозяев выставлен коэффициент 1.47, на ничью — 4.7, П2 — 7.4:
1 / 1.47 + 1 / 4.7 + 1 / 7.4 = 0.6803 + 0.2127 + 0.1351 = 1.0281 (102.81%).
Маржа — 2.81%. Это показатель ниже среднего для такого рейтингового события. Его можно сравнить с данными других популярных лицензионных операторов.
| Название БК | П1 | Х | П2 | Маржа |
|---|---|---|---|---|
| Леон | 1.47 | 4.94 | 7.20 | 2.16 |
| Винлайн | 1.43 | 4.89 | 6.60 | 5.53 |
| 1хСтавка | 1.45 | 5.0 | 7.2 | 2.85 |
| Бетсити | 1.45 | 4.7 | 6.9 | 4.73 |
| Фонбет | 1.45 | 4.7 | 6.9 | 4.73 |
| Париматч | 1.42 | 5.0 | 7.2 | 4.31 |
Почему игроки выбирают Pin UP ru
Бетторы отдают предпочтение молодому букмекеру по целому ряду причин:
- Многочисленные бонусы и акции с крупными денежными вознаграждениями.
- Привлекательная линия.
- Хорошие условия игры в разделе «Киберспорт».
- Постоянно проводятся викторины с высокими призовыми.
Регистрация и верификация
Сперва надо совершить 2 действия на сайте:
- В правом верхнем углу главной страницы размещена кнопка «Регистрация». При ее нажатии всплывает отдельное окно, где надо вписать свой номер своего телефона. На него придет СМС с кодом, который надо указать в специальной графе, и затем заполнить строку с email. После согласия с ознакомлением с правилами конторы регистрация считается завершенной.
- В течение нескольких секунд на указанный email придет письмо со ссылкой для подтверждения почты.
Ставки можно делать только после прохождения идентификации.
Букмекер предусмотрел три способа верификации:
- Через сайт оператора — надо загрузить фото с основным разворотом паспорта и селфи в руках с ним, затем вручную ввести свои личные данные с указанием ИНН.
- Через портал государственных услуг РФ.
- В салонах CONTACT (процедура платная — 150 рублей), офисах «Связной» — за 300 RUB, «МегаФон» — за 200.
Два первых способа предоставляют статус «Начальный». Он предусматривает ограничения на проведение денежных операций:
- До 60 000 RUB за одну транзакцию.
- Не более 200 000 рублей в общей сложности на ввод и вывод денег в течение месяца.
При верификации последним способом предоставляется статус «Полный». Здесь нет никаких финансовых ограничений.
Линия и роспись
Онлайн ставки на спорт в БК Pin UP ru можно оформить более чем на 25 игровых дисциплин. Предпочтение отдается футболу, киберспорту, теннису и хоккею. Рейтинговые турниры по данным категориям отображаются на главной странице официального сайта.
Выбор состязаний огромный — от топовых соревнований до молодежного футбольного чемпионата Алжира, второй хоккейной лиги Германии, матчей мужского баскетбольного дивизиона Бахрейна.
События расписаны всеми видами ставок:
- Основные.
- Комбинированные.
- Широкий выбор статистических вариантов.
- Глубокая дополнительная роспись.
- На игроков.
- Долгосрочные.
Ставки на спорт в Pin UP ru
Официальный сайт букмекерской конторы Pin Up ru сразу открывается на спортивный раздел. Здесь можно отыскать не только прематчевую линию на еще не начавшиеся противостояния. В центральной части открытой страницы отображаются и все текущие встречи.
Прематч
Широкую линию имеют не только приоритетные виды спорта. В волейболе можно поставить на Кубок Туниса или Вьетнама, в гандболе — на многие вторые европейские лиги. Роспись низкорейтинговых событий зачастую ограничивается основными видами пари и комбинированными вариантами.
При помощи фильтра «Сортировать» можно выбрать определенную группу для отображения в линии.
В БК удастся оформить ставку на:
- Футбол — фолы, угловые, желтые карточки, удары в створ ворот, офсайды.
- Хоккей — броски (блокированные), вбрасывания, 2-минутное штрафное время.
- Теннис — эйсы, двойные ошибки.
- Баскетбол — штрафные броски, подборы, перехваты.
Предусмотрен «чек-редактор». Он позволяет заменить один из исходов в экспрессе по такому же коэффициенту до начала самого раннего события по ставке.
Live
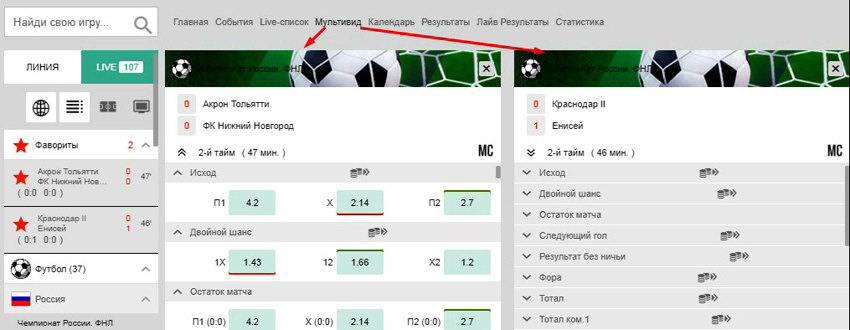
Даже в будние дни букмекер Pin UP ru выставляет линию более чем на 100 текущих событий. Для отслеживания изменений коэффициентов сразу нескольких матчей можно воспользоваться инструментом «Мультивид».
Слабопопулярные противостояния расписаны основными и комбинированными вариантами пари. В рейтинговых встречах помимо этого есть возможность поставить на статистику и дополнительную роспись.
Многие состязания удастся просматривать по видеотрансляции. Доступен графический матчтрекер, который отображает ход событий и текущую статистику.
Ставка принимается до 6 секунд — это слишком долго для скоротечных видов спорта.
На что можно ставить
Букмекер принимает ставки на традиционный и виртуальный спорт.
Спортивные соревнования
Оператор не ограничивается популярными категориями. Линия выставляется на события по мото- и велоспорту, боксу, бейсболу, регби, дартсу, гольфу, снукеру, сквошу, водному поло. Многие обозначенные виды дисциплин представлены только рейтинговыми турнирами. Но здесь букмекер учитывает их слабую популярность.
Киберспорт
БК Pinup ru предлагает сыграть в рамках нескольких дисциплин:
- Counter-Strike: Global Offensive.
- Dota 2.
- League of Legends.
- Call of Duty.
- StarCraft II.
- Valorant.
- Rainbow Six.
- Overwatch.
В линии можно увидеть турниры не только глобального, но и регионального уровня.
Рейтинговые события имеют привлекательную роспись.
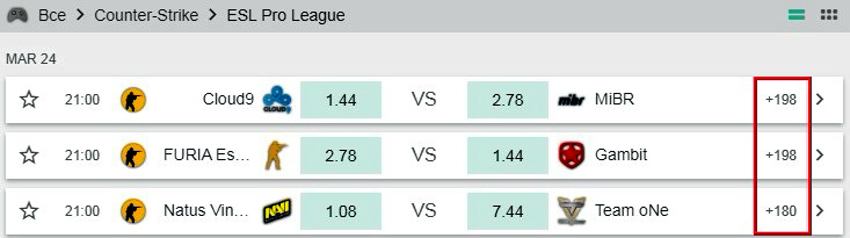
Counter-Strike: Global Offensive
Популярные противостояния CS:GO расписаны почти 200 маркерами: исходы, форы и тоталы всего матча и каждой карты по отдельности, будет ли эйс, убийство ножом, победитель пистолетного раунда.
Маржа в рейтинговых встречах составляет 5-6%.
В рамках киберспортивных дисциплин контора периодически предлагает принять участие в привлекательных бонусных программах.
Личный кабинет
Вход в букмекерскую контору Pinup ru на официальном сайте расположен в верхнем правом углу главный страницы. После авторизации в Личном кабинете доступны следующие функции:
- Просмотр истории ставок.
- Подача заявки на вывод и пополнение.
- Настройка аккаунта.
- Получение уведомлений БК.
- Внесение изменений в личные данные.
- Подача запроса в саппорт.
Мобильная версия
Весь функционал основного портала доступен и на мобильной версии:
- Оформление пари.
- Использование бонусов.
- Пополнение счета и вывод денег.
- Обращение в СП.
- Просмотр текущих событий по видеотрансляции.
Скачать клиент Pin UP ru
Для повышения скорости работы сайта необходимо скачать и установить соответствующее приложение. Вот только молодой оператор лишь в январе 2021-го разработал ПО для Android.
Для Android
Скачать приложение можно прямо на сайте компании. Чтобы телефон не блокировал установку ПО, надо в настройках дать разрешение на загрузку из неизвестных источников. Приложение не занимает много памяти и позволяет пользоваться всеми функциями основной варианта сайта БК. Поддерживаемая версия Android — 4.4 и выше.
Стоит отметить, что букмекерская компания Pin-Up также сохранит все свои спонсорские активы. Таким образом БК Ivanbet будет партнером трех футбольных клубов: «Ротора», «Шинника» и «Амкара».
пин ап казино полностью соответствует российским законам. Это значит, что все ставки легальные, а на платформе нет запрещенных азартных игр. Провайдеры интернета не имеют причин для блокировки сайта, поэтому зеркало для БК LigaStavok не требуется.
Condividi su email
Из-за блокировок сайта локальными интернет-провайдерами могут возникать проблемы со входом на азартную площадку. Иногда попасть на главную страницу интернет казино невозможно из-за технических работ. Решить проблему помогает зеркало Пин Ап. Это 100%-ная копия обыкновенного сайта казино, которая имеет отдельное доменное имя. Рабочее зеркало Пин Ап дает возможность обойти региональные блокировки и легко выполнять вход в систему 24/7. Для авторизации можно использовать привычные логин и пароль.
© Copyright 2023 ILA. All rights reserved.
Официальный мобильный клиент от одноименной букмекерской конторы. Утилита позволяет отслеживать предстоящие или актуальные спортивные события и делать ставки.
Так, например, сейчас очень многие люди подключаются к онлайн-казино, которые действительно делают повседневность очень и очень разнообразной, которые позволяют расслабляться, которые создают особую атмосферу и приносят массу позитивных впечатлений. Также стоит сказать, что самих по себе таких игровых клубов на данный момент представлено достаточное количество, но необходимо учесть, что среди них есть лучшие, в частности к ним можно отнести казино Пин Ап www.epinup.org, ведь оно предоставляет массу интересных и выгодных предложений.
Downloadable in Google Play
Попросить рабочую ссылку на зеркало сайта можно у техподдержки в чате на главной странице. Также с сылку можно найти в телеграмм канале «Pin-Up зеркало». Для этого надо нажать на аватарку, и найти в профиле ссылку на сайт Pin-Up и подтвердить переход.
Срок действия акции: не ограничен.
Так что не бойтесь играть, ведь самое главное — это вовремя остановиться.
Список запросов для поиска Как Выводить Бонусы В Пин Ап ищут:
- Ставка Pin Up Официальный
- Пин Ап Ставки Main
- Ставки На Спорт Пина Пин Ап
- Пин Ап Ставки На Спорт Официальный
- Пин Ап Ставки Онлайн На Спорте
- Лига Ставок Pin Up Вин